前言
Jenkins作为开源持续集成与持续交付(CI/CD)的领军工具,在软件开发流程中扮演着至关重要的角色。本文将详细介绍在Linux系统上安装、配置和优化Jenkins的全过程,结合具体代码示例,帮助开发者快速搭建高效稳定的自动化构建环境。
一、系统准备与环境配置
1. 操作系统要求
支持的Linux发行版:Ubuntu/Debian、CentOS/RHEL、Amazon Linux等
最低硬件配置:2GB RAM,10GB可用磁盘空间
推荐硬件配置:4GB RAM+,20GB可用磁盘空间
2. 系统更新与依赖安装
# Ubuntu/Debian系统
sudo apt-get update
sudo apt-get install -y openjdk-11-jdk wget curl gnupg2
# CentOS/RHEL系统
sudo yum update -y
sudo yum install -y java-11-openjdk-devel wget curl
3. 防火墙配置
# Ubuntu/Debian (UFW)
sudo ufw allow 8080/tcp
sudo ufw reload
# CentOS/RHEL (Firewalld)
sudo firewall-cmd --permanent --add-port=8080/tcp
sudo firewall-cmd --reload
二、Jenkins安装与初始化
1. 使用官方仓库安装
# 添加Jenkins官方GPG密钥
wget -q -O - https://pkg.jenkins.io/debian-stable/jenkins.io.key | sudo apt-key add -
# 添加Jenkins软件源
echo deb https://pkg.jenkins.io/debian-stable binary/ | sudo tee /etc/apt/sources.list.d/jenkins.list
# 更新包索引并安装Jenkins
sudo apt-get update
sudo apt-get install -y jenkins
# 启动Jenkins服务
sudo systemctl start jenkins
# 启用Jenkins开机自启
sudo systemctl enable jenkins
2. 验证安装
# 检查Jenkins服务状态
sudo systemctl status jenkins
# 查看Jenkins初始管理员密码
sudo cat /var/lib/jenkins/secrets/initialAdminPassword
# 输出示例:
# 3b8c5d8f2a9e4b7a8d9c0e1f2a3b4c5d6e7f8a9b0c1d2e3f4a5b6c7d8e9f
3. 首次访问配置
打开浏览器访问:http://your-server-ip:8080
输入初始管理员密码进行解锁
选择”Install suggested plugins”安装推荐插件
创建管理员账户并完成初始化
三、Jenkins高级配置
1. 配置Jenkins系统参数
# 修改Jenkins默认端口(/etc/default/jenkins)
HTTP_PORT=9090
# 修改Jenkins工作目录(/etc/default/jenkins)
JENKINS_HOME=/data/jenkins
# 修改JVM参数(/etc/default/jenkins)
JENKINS_JAVA_OPTIONS="-Xms512m -Xmx1024m -Djava.awt.headless=true"
# 重启Jenkins服务使配置生效
sudo systemctl restart jenkins
2. 配置反向代理(Nginx)
# 安装Nginx
sudo apt-get install -y nginx
# 创建Nginx配置文件(/etc/nginx/sites-available/jenkins)
sudo tee /etc/nginx/sites-available/jenkins <<-'EOF'
server {
listen 80;
server_name jenkins.example.com;
location / {
proxy_pass http://localhost:8080;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_redirect http:// https://;
# 增加代理超时时间
proxy_connect_timeout 600;
proxy_send_timeout 600;
proxy_read_timeout 600;
send_timeout 600;
}
}
EOF
# 创建软链接启用配置
sudo ln -s /etc/nginx/sites-available/jenkins /etc/nginx/sites-enabled/
# 检查Nginx配置
sudo nginx -t
# 重启Nginx服务
sudo systemctl restart nginx
3. 配置HTTPS(Let’s Encrypt)
# 安装Certbot
sudo apt-get install -y certbot python3-certbot-nginx
# 获取SSL证书
sudo certbot --nginx -d jenkins.example.com
# 配置自动续期
sudo crontab -e
# 添加以下内容
0 12 * * * /usr/bin/certbot renew --quiet
四、Jenkins插件管理
1. 常用插件安装
Pipeline:支持Jenkins Pipeline
GitLab Plugin:集成GitLab代码仓库
Docker Pipeline:支持Docker容器化构建
Credentials Plugin:安全管理凭证
Email Extension Plugin:高级邮件通知
Slack Notification Plugin:集成Slack通知
2. 插件安装命令行工具
# 安装Jenkins CLI
wget http://localhost:8080/jnlpJars/jenkins-cli.jar
# 安装指定插件
java -jar jenkins-cli.jar -s http://localhost:8080/ install-plugin gitlab-plugin pipeline-aws
# 重启Jenkins使插件生效
java -jar jenkins-cli.jar -s http://localhost:8080/ safe-restart
五、Jenkins Pipeline实践
1. Pipeline基础语法
pipeline {
agent any
environment {
APP_NAME = 'my-app'
DOCKER_IMAGE = 'registry.example.com/my-app'
}
stages {
stage('Build') {
steps {
echo 'Building the application...'
sh 'mvn clean package'
}
}
stage('Test') {
steps {
echo 'Running tests...'
sh 'mvn test'
}
}
stage('Docker Build') {
steps {
echo 'Building Docker image...'
sh "docker build -t ${
DOCKER_IMAGE}:${
env.BUILD_NUMBER} ."
}
}
stage('Deploy') {
when {
branch 'main'
}
steps {
echo 'Deploying to production...'
sh "docker push ${
DOCKER_IMAGE}:${
env.BUILD_NUMBER}"
sh "kubectl apply -f k8s/deployment.yaml"
}
}
}
post {
success {
echo 'Build succeeded!'
slackSend channel: '#ci-cd', color: 'good', message: "Build ${
env.JOB_NAME} ${
env.BUILD_NUMBER} succeeded!"
}
failure {
echo 'Build failed!'
slackSend channel: '#ci-cd', color: 'danger', message: "Build ${
env.JOB_NAME} ${
env.BUILD_NUMBER} failed!"
emailext (
subject: "Jenkins Build Failure: ${
env.JOB_NAME}",
body: """<p>Build failed: ${
env.BUILD_URL}</p>
<p>Please check the build logs for details.</p>""",
to: 'developers@example.com'
)
}
}
}
2. 多分支Pipeline配置
# Jenkinsfile(放置在代码仓库根目录)
pipeline {
agent {
docker {
image 'maven:3.8.4-openjdk-17'
args '-v /root/.m2:/root/.m2'
}
}
stages {
stage('Build') {
steps {
sh 'mvn clean package'
}
}
stage('Test') {
steps {
sh 'mvn test'
junit 'target/surefire-reports/*.xml'
}
}
stage('Deploy') {
when {
branch 'main'
}
steps {
// 部署到生产环境
}
}
}
}
六、Jenkins安全加固
1. 基于角色的访问控制
安装Role-based Authorization Strategy插件
系统管理 → 配置全局安全 → 授权策略 → Role-Based Strategy
系统管理 → Manage and Assign Roles
创建角色(如developers、admins)
分配权限到角色
分配用户到角色
2. 安全配置最佳实践
# 禁用匿名访问(config.xml)
<authorizationStrategy class="hudson.security.FullControlOnceLoggedInAuthorizationStrategy">
<denyAnonymousReadAccess>true</denyAnonymousReadAccess>
</authorizationStrategy>
# 启用CSRF保护
<useSecurity>true</useSecurity>
<csrf>
<class>hudson.security.csrf.DefaultCrumbIssuer</class>
<excludeClientIPFromCrumb>false</excludeClientIPFromCrumb>
</csrf>
# 配置安全更新站点
<updateSite>
<id>default</id>
<url>https://updates.jenkins.io/update-center.json</url>
</updateSite>
3. SSH密钥认证配置
# 生成SSH密钥对
ssh-keygen -t rsa -b 4096 -C "jenkins@example.com"
# 将公钥添加到GitLab/GitHub等代码仓库
cat ~/.ssh/id_rsa.pub
# 在Jenkins中配置SSH凭证
Credentials → System → Global credentials → Add Credentials
- Kind: SSH Username with private key
- Username: jenkins
- Private Key: From the Jenkins master ~/.ssh/id_rsa
七、Jenkins性能优化
1. JVM参数优化
# 修改JVM参数(/etc/default/jenkins)
JENKINS_JAVA_OPTIONS="-Djava.awt.headless=true -Xms1024m -Xmx2048m -XX:MaxPermSize=256m
-XX:+UseG1GC -XX:G1HeapRegionSize=4M -XX:+HeapDumpOnOutOfMemoryError
-Djenkins.install.runSetupWizard=false"
2. 构建节点配置
# 添加构建代理节点
1. 系统管理 → 节点管理 → 新建节点
2. 配置节点属性(标签、执行器数量等)
3. 选择启动方式(SSH、JNLP等)
4. 配置节点工作目录
# 示例:通过SSH添加节点
- 远程FS根目录:/home/jenkins-agent/workspace
- 标签:linux-node
- 启动方式:通过SSH启动代理
- Host:192.168.1.101
- Credentials:jenkins-user (SSH密钥)
3. 磁盘空间管理
# 清理旧构建记录
java -jar jenkins-cli.jar -s http://localhost:8080/ groovy = <<EOF
Jenkins.instance.items.each { job ->
job.builds.findAll { build ->
build.number < (job.builds.size() - 10)
}.each { build ->
println "Deleting build ${job.name} #${build.number}"
build.delete()
}
}
EOF
# 配置工作空间清理策略
在Job配置中 → 构建环境 → Delete workspace before build starts
八、备份与恢复策略
1. 全量备份脚本
#!/bin/bash
# Jenkins备份脚本
# 配置参数
JENKINS_HOME="/var/lib/jenkins"
BACKUP_DIR="/data/backup/jenkins"
MAX_BACKUPS=10
# 创建备份目录
mkdir -p $BACKUP_DIR
# 生成备份文件名
BACKUP_FILE="$BACKUP_DIR/jenkins_backup_$(date +%Y%m%d_%H%M%S).tar.gz"
# 停止Jenkins服务(可选)
# systemctl stop jenkins
# 创建备份
tar -zcvf $BACKUP_FILE $JENKINS_HOME --exclude="$JENKINS_HOME/workspace" --exclude="$JENKINS_HOME/caches"
# 启动Jenkins服务(可选)
# systemctl start jenkins
# 删除旧备份
cd $BACKUP_DIR
ls -t | tail -n +$((MAX_BACKUPS + 1)) | xargs -I {
} rm -f {
}
echo "Backup completed: $BACKUP_FILE"
2. 恢复操作步骤
# 1. 停止Jenkins服务
sudo systemctl stop jenkins
# 2. 备份当前Jenkins目录(以防万一)
sudo cp -r /var/lib/jenkins /var/lib/jenkins.bak
# 3. 解压备份文件
sudo tar -zxvf /data/backup/jenkins/jenkins_backup_20230515_100000.tar.gz -C /
# 4. 恢复权限
sudo chown -R jenkins:jenkins /var/lib/jenkins
# 5. 启动Jenkins服务
sudo systemctl start jenkins
总结
本文详细介绍了在Linux系统上安装和配置Jenkins的全过程,包括:
系统准备与依赖安装
Jenkins的安装与初始化
高级配置(反向代理、HTTPS)
插件管理与Pipeline实践
安全加固策略
性能优化技巧
备份与恢复方案
通过这些步骤,开发者可以搭建一个安全、高效、稳定的Jenkins CI/CD平台。建议在实践中持续优化配置,定期更新插件和系统,确保Jenkins环境的安全性和可靠性,从而提升软件开发的效率和质量。










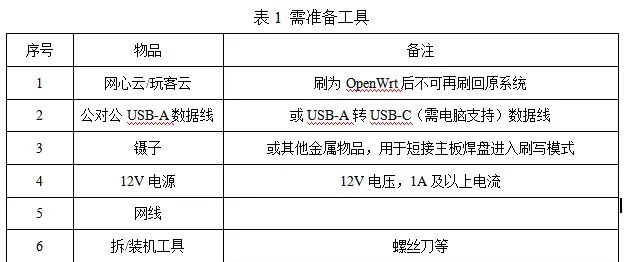








暂无评论内容